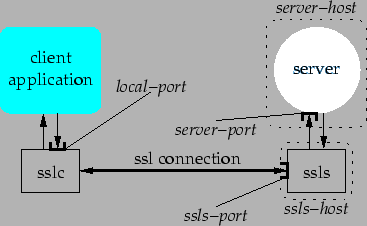
 |
sslc local-port ssls-host[/ssls-name] ssls-port remote-host remote-port ca-certificate [sslc-certificate sslc-priv-key]
ssls ssls-port ca-certificate [name...]
the parameters are:
| local-port | port on which sslc accepts connections from client applications |
| ssls-host | host running the remote endpoint ssls |
| ssls-name | name of the server used for authentication. This parameter is optional. You may choose not to support it at all, or to support it as an optional parameter. |
| ssls-port | port on which ssls accepts connections from sslc |
| remote-host | host running the server application, to which ssls connects to establish the tunnel |
| remote-port | port on which the server application accepts connections |
| ca-certificate | file containing the certificate of a trusted certification authority, serving as a trust anchor. |
| sslc-certificate | file containing client's certificate (optional) |
| sslc-priv-key | file containing client's certificate (optional) |
| name... | optional list of authorized subjects. |
The architecture of the tunnel is shown below in Figure 1:
 |
It is not required that sslc and ssls handle multiple tunnels at the same time. In order to test your implementation you may want to use a simple client/server application. I suggest you use a web browser, pointing sslc to any web server, and pointing the web browser to your sslc.
When run with one or more name parameters, the server (ssls) will authenticate the client (sslc) by:
I (Antonio) will be your certification authority. Use this certificate as a trust anchor for both your client and server. In order to obtain valid certificates for your implementation, you must create certificate requests and send them to me by e-mail (to [email protected]). I will sign off your requests and return the corresponding X.509 certificate to you (by e-mail.)
Note that if you choose not to implement the optional ssls-name parameter (within the client), then your server certificate must match the host name of the host on which you run the server, since you are using the ssls-host parameter both as an address and a name.
You must turn in your assignment in a single package, in the form of a TAR file (compressed with gzip if you like) or a ZIP file. Please, include the following in your package:
Please, do not include the OpenSSL library in your package.
You must send the package as a MIME-compatible attachment to [email protected].